Core Aspects of Digital Assets, Cryptocurrencies, and Blockchain
Below is a collection of frequent topics discussed by the 1881 Capital team
I. What Makes Blockchain Technology Different From What We Have Today?
II. Are Most Digital Assets Variations Of Bitcoin?
III. What Stops Fraudulent Transactions On The Blockchain?
IV. How Does The Blockchain Know Who’s Doing the Transaction If It’s Anonymous?
V. Who’s Actually Using this Technology, Or Is It All Speculation?
What Makes Blockchain Technology Different From What We Have Today?
Today, most transactions and data transfers are recorded through centralized databases. These databases are efficient as they simply require updating spreadsheets or tables in a database management system (DBMS). For example, a small business that manufactures shoes can quite effectively manage inventory through an Excel spreadsheet or a DBMS — as one pair of shoes is sold, the business adjusts its own internal records, or debits cash and credits inventory.
The shoe manufacturer does not require blockchain technology. In fact, incorporating blockchain technology could complicate its business and add unnecessary, cumbersome features. At its core, blockchains are distributed databases that update their data across multiple computers such that once the computers agree to update the data, the data is then permanent. In this example, the shoe manufacturer has no need to update its inventory across multiple computers as one computer and a DBMS works just fine.
But what if the shoe manufacturer wants to do more than just understand its own internal inventory from a centralized database? What if it wants to provide facts about their operations so that outsiders can easily discern its value? What if it wants to thoroughly understand its supply chain, proving that its raw materials were sourced sustainably, providing product authenticity to consumers, all while having multiple sources agree that this information is accurate?
This is where blockchain technology begins to show its advantages; albeit this is just one flavor of blockchain. The aforementioned shoe manufacturer, Nike, recently launched a blockchain initiative to prove the authenticity of its products, an issue that has been plaguing them for years. In fact, 88% of the world’s counterfeit sneakers are Nike, which totals about $500 billion in value. Nike would love to prevent some of this value leak.
In order to do so, Nike introduced blockchain technology to help consumers know if they were receiving an authentic pair of Nike shoes, or rather, prove the shoes’ provenance. Consumers can tap on an embedded chip within the shoe with a smartphone and then view specific details such as style, shipping origin, and manufacturing timestamp, which are all viewable and verifiable on the blockchain. The blockchain is the ideal database infrastructure for this verification because it cannot be tampered with. Blockchains excel because of two main properties: transparency and immutability.
Transparency allows everyone with access to the blockchain to view full details of all data stored on the blockchain. For public blockchains anybody can view these details although certain information is anonymized (discussed more in Topic 4). Immutability, or being unchangeable, is also critical when it comes to securing these intricate public blockchain systems. The immutability comes, in part, from the magic of “hashing”, or data fingerprinting, which we discuss in more depth in Topic 3.
Going back to Nike, all of the supply chain inputs, such as style, shipping origin, and manufacturing timestamp result in a unique verifiable output that can be seen on the blockchain. Consumers can then scan the aforementioned chip embedded in their Nike shoe, which is another data input to the blockchain, and verify with complete accuracy that they own authentic Nike shoes. This technology can be quite valuable for someone spending over $100,000 on shoes.
This example just illustrates one potential use case of blockchain technology. It also alludes to how in the future blockchains can improve value chains and reveal the value and cost at each step of the supply chain. Furthermore, the example incorporates two different technologies — blockchain technology in concert with the embedded Near-Field Communication chip in the shoe. This distinguishment is significant because many of the “aha” use cases for blockchain result from the combination with other technologies.
To spark the imagination, below is a list of some other popular combinations:
· Blockchain and Augmented Reality (AR) — Blockchain securely records the ownership and provenance of digital assets in virtual and augmented reality environments
· Blockchain and Cloud Computing — Blockchain ensures the integrity of data stored in the cloud by providing a tamper-proof record of all data transactions
· Blockchain and Artificial Intelligence (AI) — Blockchain provides immutable and auditable data to AI and ML models
· Blockchain and Biometrics — Combining blockchain with biometric authentication enhances the security and privacy of digital identities to provide a tamper-proof record of ID
· Blockchain and Big Data — Blockchain enables decentralized marketplaces for buying and selling big data, allowing for secure and transparent transactions
· Blockchain and Internet of Things (IoT) — Combining blockchain with IoT devices allows users to securely record and manage data from smart home appliances or city infrastructure
Are Most Digital Assets Variations Of Bitcoin?
As described in the first section, blockchain use cases can take different shapes and sizes. For each different use case, there may be a logical extension where a cryptocurrency or token makes sense to be involved in the dynamics of the network. For example, the first blockchain in existence, Bitcoin, had a highly relevant need for a digital asset on its network — “bitcoin” or “BTC” — as the primary purpose of Bitcoin is to display bitcoin ownership on the blockchain. In a no-frills way, the Bitcoin blockchain was built with the sole purpose of being a transparent and verifiable database that tells you “This address owns 0.002 BTC; another address owns 22 BTC.”
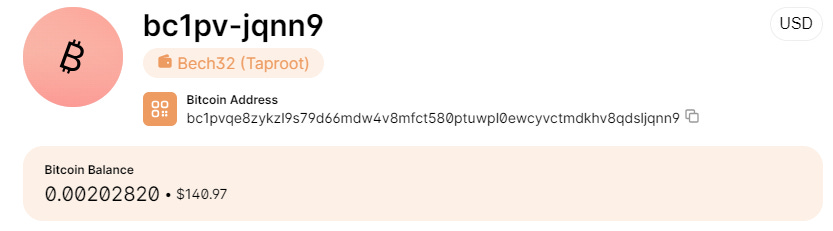
Bitcoin has done quite well at this singular use case because people started to see value in it from a monetary perspective. This cultural and psychological phenomenon has earned Bitcoin the title of Digital Gold and has made it the store of value leader across all digital assets.
However, not all digital asset projects attempt to be a store of value or currency, although they may still be called cryptocurrencies. Some digital assets function much more similarly to a commodity, coupon, or a real-world representation of something.
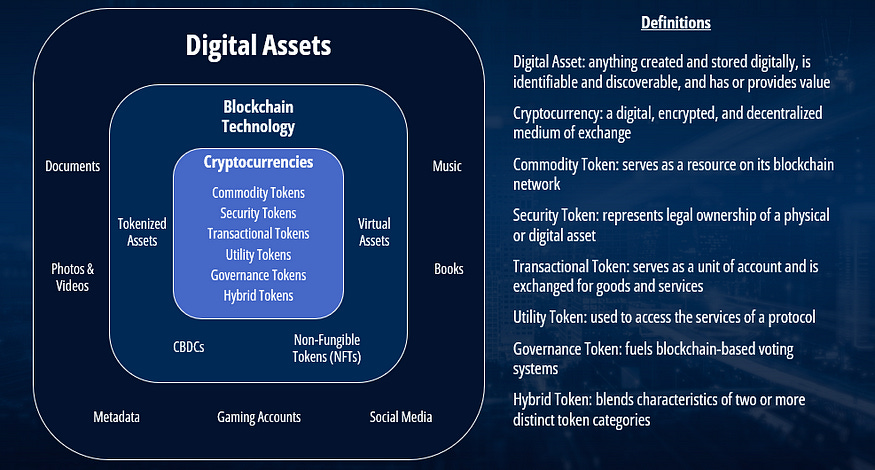
Just as a barrel of WTI Crude Oil has a monetary equivalent, it shouldn’t be thought of as a United States Dollar, although it can be exchanged for a dollar.
So, what are the leading digital asset commodities? Ether (ETH) on the Ethereum network is the commodity that is required to run operations on the Ethereum blockchain. There are 120 billion ETH circulating globally, which equates to a total valuation of over $400 billion for the network. Ethereum is the second largest digital asset by market cap behind Bitcoin at $1.3 trillion.
The Ethereum network is particularly different from Bitcoin in that Ethereum’s goal is to support more functionality on its blockchain infrastructure (and not just be a store of value). To be explicit, Bitcoin is a pure cryptocurrency, representing a currency, and Ether is a commodity token with numerous value propositions.
For example, a user can download an Ethereum wallet to their internet browser, acquire ETH, and then deposit that ETH into a lending application. Through zero human interaction, the user can then acquire “digital USD” and proceed to purchase items from online retailers. The digital representation of USD is also called a stablecoin or a transactional token.
However, there are more than just lending applications on Ethereum. Marketplaces, games, social platforms, exchanges, and others are also popular. As more applications build on the Ethereum network, they must utilize the ETH digital asset as it is the commodity underpinning operations. For example, if you wanted to interact with the aforementioned lending application then you would need to spend ETH to make the transaction happen. In this sense, ETH can be thought of as the crude oil that makes the machine run (transaction fees are actually called gas on the Ethereum network — here’s the original list of actions and corresponding amount of gas needed for that action)
Although, notably, Ethereum serves as a home for other applications to accrue value too. Projects are free to deploy their own unique digital asset that can become valuable. For instance, Chainlink is the leader in bringing data from the real-world into the blockchain ecosystem — a highly sought after service as blockchain networks have no way of sourcing external data onto the chain. Chainlink’s token (LINK) is a utility token and it accrues value as consumers will pay to receive the utility of this real-world data. Chainlink has built a competitive advantage against its peers because it is known as the most reliable and extensive provider of outside data.
Going one step further, the Aave Protocol and the accompanying digital asset, AAVE, generates value by partnering with Ethereum, Chainlink, and other blockchain networks. Aave was first deployed on the Ethereum network in January 2020 and has since grown to the largest decentralized lending platform in the world with over $21 billion in assets lent and borrowed. Aave benefits from Chainlink as it needs reliable prices for the hundreds of different digital assets on its platform to determine the value of collateral and borrowed assets. The AAVE digital asset gains from the reliability of both Ethereum and Chainlink and independently garners value as more people use its platform.
This Value Net of digital asset companies and their respective value propositions is just one example of hundreds that exist within the broader digital asset ecosystem. Each protocol is vying to gain value in its own unique way by providing different goods and services with different intentions. Just as we saw with the internet boom, some will turn out to be Pets.com while others are Amazon…
What Stops Fraudulent Transactions On The Blockchain?
Bitcoin was the first digital asset to “go-to-market” and foundationally structured its blockchain so that transactions couldn’t be changed after they occurred. As mentioned earlier, the goal was simple — “tell me what account owns bitcoin and tell me how much they own.” People would never trust storing their savings on it if that number could accidentally change. The number should only change if the owner of that account intentionally decides to deposit or withdraw from that account.
So how can the number change only when the owner wants it to change, and on top of that, the number needs to be correct across the entire network? The answer resides in the one form of universal communication that everyone can agree on regardless of one’s backgrounds or beliefs… math. If you ask what is “2+2” to a crowd of (sane) individuals, each individual should answer “4,” regardless of their backgrounds. You would get an even more consistent answer if you asked a group of computers.
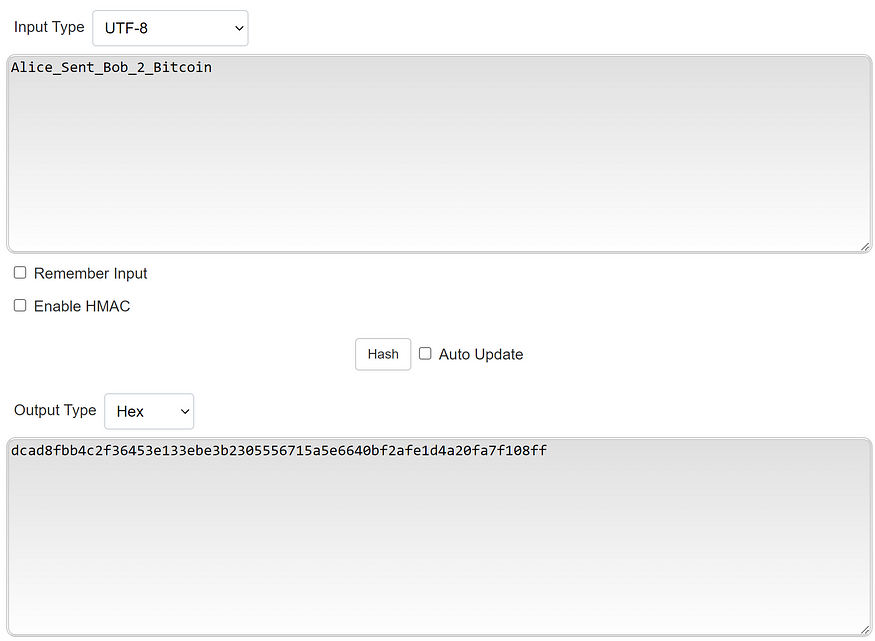
Hashing, which we introduced in Section 1, is the key to this mathematical, universal communication. Hashing takes an input such as a string of characters — “Alice_Sent_Bob_2_Bitcoin” — and returns a fixed-size string of characters. That previous string of characters inputted into a hash function returns an entirely different output if you change any part of it. Additionally, it is nearly impossible to work backwards and guess the input. Try it out here. (In computer code, the actual string of characters would look like e7d3fbb1836d4e1d45b1edb2c6a)
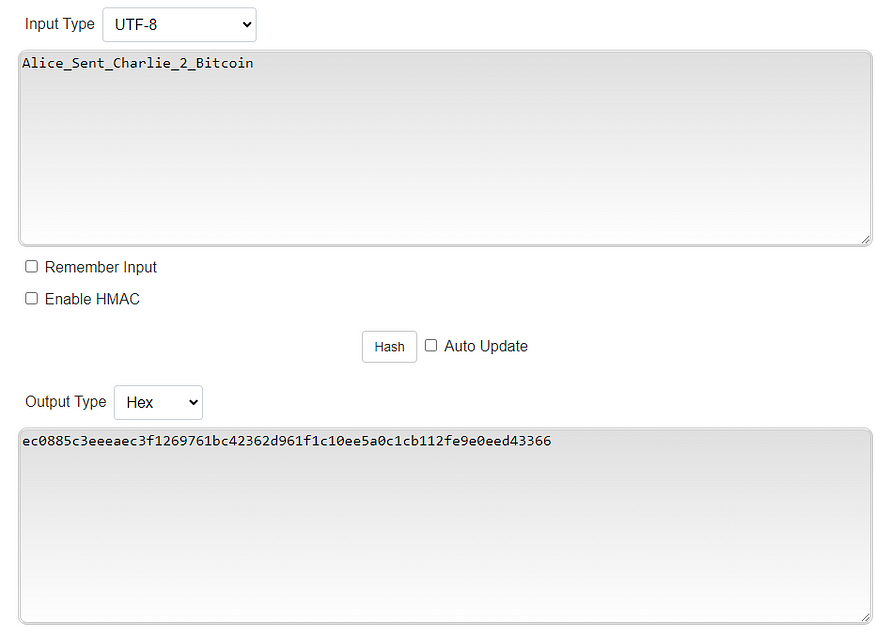
This subtlety is quite important as changing the string of characters, or rather, changing the transactions contained in the string of characters, results in an entirely different output.
Note, blocks in a blockchain are just a list of transactions. Adding a new block requires hashing the previous block, which then creates a unique output that is then inserted into the next block.
So, hashing all of the transactions contained in Block A creates a unique output that can then be stored in Block B, subsequently impacting the output stored in Block C. This property becomes monumental when you need computers around the world to come to the same answer. Even more so, computers around the world can look at the current Bitcoin network, hash the data, and come to the same answer as to what transactions occurred. Ultimately, changing anything stored in Block A, B, or C will cause a chain-reaction event that affects all of the Blocks, or rather the “blockchain” and it is a defining achievement of the technology.
Given that guessing the input to a hash function based on the output is nearly impossible, this effectively locks those transactions in perpetuum to the blockchain. Computers in the blockchain system can work together to leverage the hashing to create an honest, objective account of the state of the distributed ledger.
However, what if a computer in the network lies? Can it screw up the entire ledger or steal from it? First, it’s worth pointing out that the irreversibility of the hashing function makes it economically prohibitive for a computer to lie. However, “not lying” is not enough — the computers should be incentivized to tell the truth. That’s where a financial incentive comes into play. You need a system that forces all computers to want to tell the truth, and it needs to be rewarding enough so that these computers never try to insert a fake transaction that could be more financially rewarding.
One solution to this game theoretic scenario is to have the computers compete for a financial reward, and have the reward go to computers that gave an honest account of the most recent transactions. Additionally, adding a cost to compete makes it prohibitively expensive to try to manipulate the system.
You’ve now designed a system where all of the computers are now incentivized to tell the truth! This is perfect if you just want to answer the question — “tell me what address owns bitcoin and tell me how much they own.” Ultimately, this design is referred to as Proof of Work — computers must work to earn the financial reward while giving an honest account of transactions on the network.
This isn’t the only way to get computers to tell the truth. You may have heard of Proof of Stake, which is another incentive structure to reward computers for telling the truth. In a Proof of Stake system, the financial reward is structured differently — computers, called validators, lock the native digital currency to the blockchain and are chosen to add the new block based on the number of staked coins that they have. The chain rewards validators who honestly validate the blocks. However, since this form of consensus is less computationally intensive than Proof of Work (meaning that there is less cost and thus less of an economic deterrent to lie), this incentive structure also punishes validators who try to cheat the system.
How Does The Blockchain Know Who’s Doing The Transaction If It’s Anonymous?
Blockchain systems work because of cryptography. The word cryptography comes from the Greek words kryptos, meaning hidden, and graph, meaning to write. The name itself implies hiding information in order to facilitate transactions on these networks.
Furthermore, our “real world” identities are obscured in blockchain systems, or rather, pseudonymous. Suppose we have Alice and Bob. If Alice were to send $100 to Bob via a bank wire, her bank will know that Alice is sending the funds to Bob’s bank account. However, if she were to do this transaction via the Bitcoin network (or any blockchain network, for that matter), the Bitcoin network does not know that “Alice” is sending the money to “Bob”. However, Alice and Bob both have unique digital identifiers, called addresses, on the blockchain. These unique digital identifiers are used to send, receive, and hold digital assets in these blockchain systems.
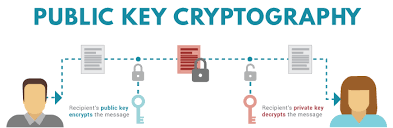
This invites an important question. What’s preventing a malicious actor from intercepting Alice’s transfer to Bob so that he can receive the funds instead? This is where the fundamentals of cryptography start to become very important. When you create an address on the blockchain, the user generating the address is given a private key. From this private key, a public key is then derived via a security algorithm. As the names imply, the private key is known only to the user while the public key is known by the network. The security algorithm is designed in a way such that it’s not reversible, meaning that while you can derive the public key from the private key, it is practically impossible to reverse engineer the private key from the public key — a true one-way street.
These private keys and public keys are foundational in securing the blockchain system and ensuring that bad actors cannot intercept messages and usurp funds for themselves. When Alice sends Bob funds on a blockchain network, she uses Bob’s public key to encrypt the transaction. Only Bob, with his private key, can decrypt the message and accept the funds from Alice. Therefore, it’s helpful to think of Bob’s private key as a way to prove that he owns the address. A bad actor intercepting Alice’s transfer to Bob would only see a bunch of gibberish, and therefore, can’t cheat the system to steal the funds.
A significant point to call out, however, is that if the attacker were to somehow figure out Bob’s private key (if Bob were careless with managing it, for instance), then the security falls apart. The attacker, by owning Bob’s private key, can now prove to Alice and the blockchain system that he is, in fact, Bob. This is why it’s important to never share your private keys with anybody. If you use your own wallet, store the private key in a place that only you would be able to access it.
Within a blockchain, the addresses are enough for the system to uniquely identify who’s transacting in its ecosystem. The computers powering these systems work together using the consensus mechanisms described in Section 3 to create a record of transactions that have occurred in the blockchain. These computers, nor the system, care about the real world identities; the accounting information across the addresses suffices.
To connect blockchain addresses to real world identities, digital asset exchanges have built their own internal databases to map an individual to her/his address on the blockchain. For instance, if Alice purchases Bitcoin using Coinbase, an address (let’s say A1B2C3D4) is created in the Bitcoin network. The Bitcoin network doesn’t know, or even care, that A1B2C3D4 belongs to Alice. It simply uses this address for its record-keeping. Coinbase, however, keeps its own internal record indicating that A1B2C3D4 is owned by Alice, serving as the identity bridge from the blockchain world to the real world.
Who’s Actually Using This Technology, Or Is It All Speculation?
The media and blockchain skeptics might have you believe that public blockchains are used only for speculation, gambling, and illicit activities. While this asset class, as well as other asset classes, has had its fair share of bad actors, the vast majority of use cases are legitimate and are utilized by legitimate actors (Unfortunately, new technologies can often serve as a medium for scammers just like the early days of email).
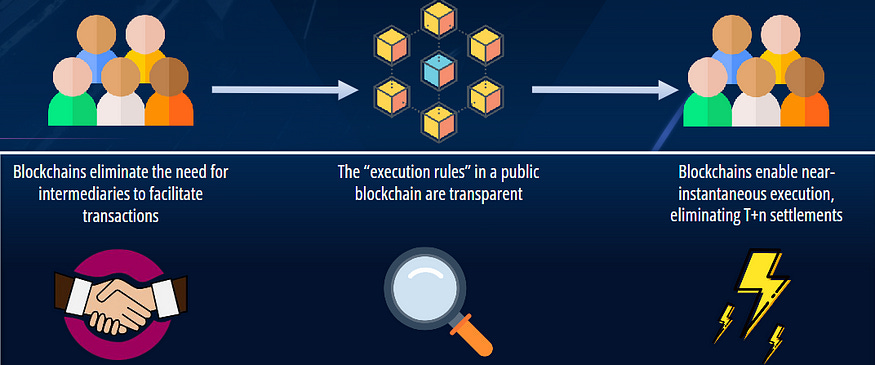
Ultimately, with a public blockchain, you have the power to replace a trust-based system of intermediaries with a distributed ledger powered by cryptography. The network of computers guarantees the truth of the system. The two main benefits of this truth-based system are cost savings and time savings. The intermediaries, who demand payments for themselves and who take their time to reconcile the processes on their end, are replaced by code — code that is cheap and fast. Any highly intermediated process is ripe for disruption through public blockchains, and many well-established institutions are figuring this out and are starting to replace their expensive, time-consuming trust-based processes with a blockchain backend.
One notable example is Siemens, who issued a digital bond on the Polygon blockchain worth 60 million Euros. Issuing this digital bond on the blockchain has allowed Siemens to eliminate the need of an intermediary as a bank. Since the bond is digitally verified, Siemens sold the instrument directly to its investors. Transactions were also executed much more quickly and efficiently due to the effectiveness of the public Polygon blockchain.
Serial technology entrepreneur Mike Cagney, who founded SoFi Digital Bank, shifted his focus to the blockchain with his next startup, Figure Technologies. Figure, which utilizes the Provenance blockchain as its backend, has facilitated the creation and usage of digitally native mortgages. Auditors such as KPMG and PWC can save significant time and money to verify these digitally native mortgages, since they would simply need to verify the cryptographic hash of the contract. This makes the securitization of these mortgages much more efficient as well, allowing banks to take advantage of the streamlined verification process.
So these technologies can disrupt the financial world… but do they have any value beyond that?
Absolutely. And this is where these technologies start to get really fun. You may have heard of JJ Abrams, one of the most prominent science fiction directors today. His production company, Bad Robot Productions, is responsible for the recent Star Trek and Star Wars movies as well as the hit TV show Westworld. It turns out that Bad Robot is also a prominent user of the Render network. The Render network is the first decentralized GPU rendering network and allows content developers to leverage GPU compute power. Bad Robot has used the Render network to purchase GPU computation to render complex visual effects. Without this blockchain network, the production company would have had to run its own GPUs, an expensive and time-consuming acquisition.
DePIN, or decentralized physical infrastructure networks, is another unique use of blockchain ecosystems that can apply to a wide variety of use cases. The idea behind DePIN is that blockchain systems can be used to improve security, transparency, and efficiency in physical infrastructure. By incorporating physical infrastructure into a blockchain ecosystem, we really start to see the different uses for blockchain technology and digital assets — and dismiss the idea that blockchain and digital assets are just pure speculative investments.
The Render network is itself an example of a DePIN, since it helps content producers to physically use GPU resources. DePINs can also be used in supply chain applications to prove product provenance and establish trust in the product delivery process. These systems can help democratize the use of physical infrastructure and “hard” assets. As another example, the Helium network allows any individual running a Helium Hotspot to earn rewards for providing wireless network coverage.

The potential benefits of blockchain technology and digital assets, including democratization, access, and transactions that are better, faster, safer, and cheaper, will be available to everyone, from the largest multinational corporations to the smallest individual. With the continued growth and maturation of this industry, we envision blockchain technology and digital assets becoming an integral part of everyone’s day-to-day life (and they may not even know it).
Disclosure: The information provided on this blog is for general informational purposes only and is not intended as, nor should it be considered as, financial, investment, tax, or legal advice. 1881 Capital Partners Management, LLC makes no representation as to the accuracy, completeness, or timeliness of the information, and disclaims any liability for any errors or omissions.
All opinions expressed on this blog are solely those of the authors and do not necessarily reflect the views of 1881 Capital Partners Management, LLC or any of its affiliates.
1881 Capital Partners Management, LLC is not responsible for any third-party content that may be accessed through this blog. Any links to third-party sites are provided for convenience only and do not imply endorsement or approval by 1881 Capital Partners Management, LLC of the content on those sites.